MEC Sandbox Help: Difference between revisions
No edit summary |
|||
| Line 70: | Line 70: | ||
UEs move along their pre-defined path, triggering changes in connectivity and in MEC Service outputs (responses & notifications). | UEs move along their pre-defined path, triggering changes in connectivity and in MEC Service outputs (responses & notifications). | ||
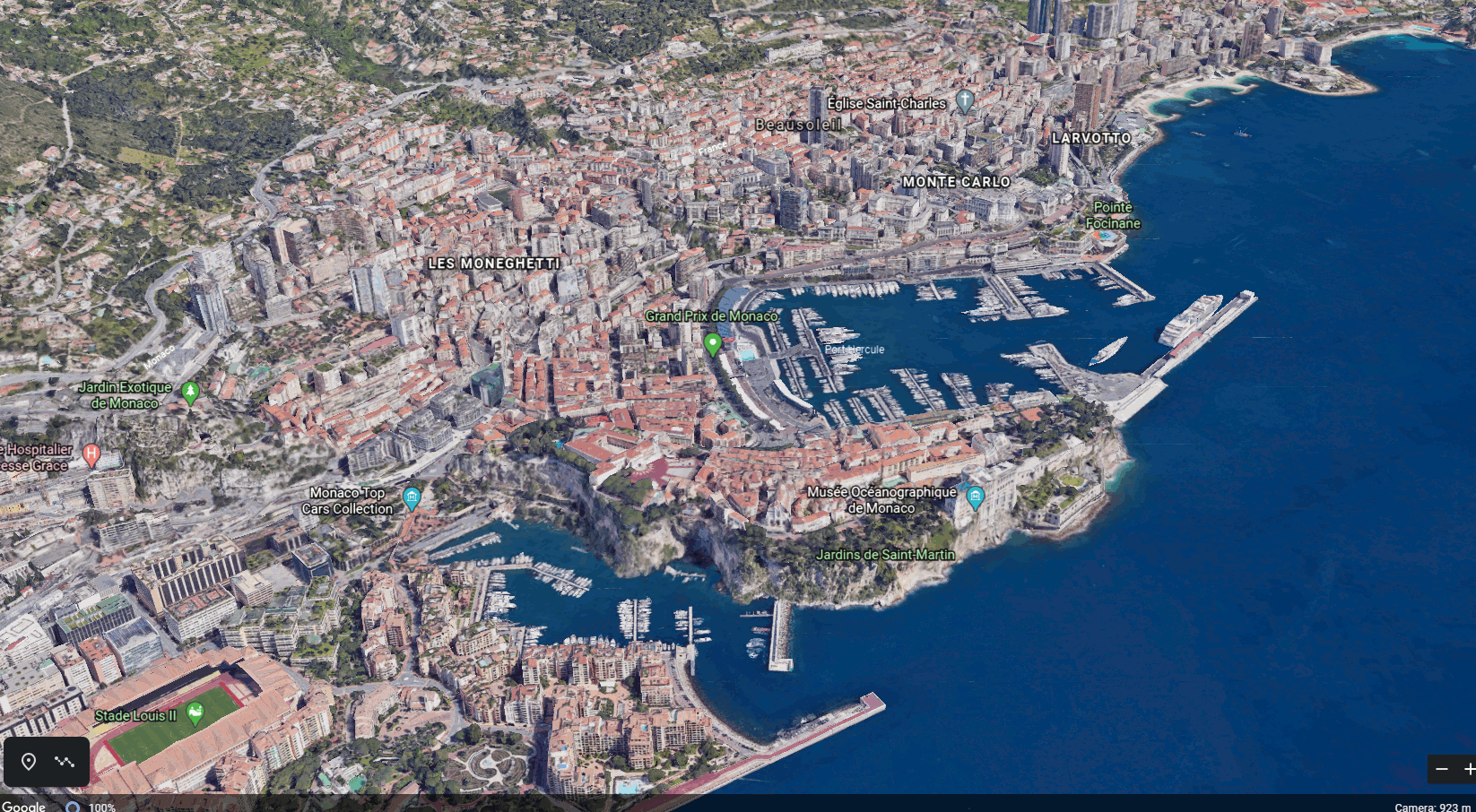
The city of Monaco was chosen as the simulated location. | The city of Monaco was chosen as the simulated location as shown on right. | ||
| style="width: 50%; text-align:center;" |[[File:Monaco-3D-Satellite.png|border|500x500px]] | | style="width: 50%; text-align:center;" |[[File:Monaco-3D-Satellite.png|border|500x500px]] | ||
|} | |} | ||
Revision as of 00:54, 5 December 2020
Platform Concepts
MEC Sandbox is an interactive environment that enables users to learn & experiment with ETSI MEC Service APIs. These standardized RESTful APIs are targeted towards MEC application developers to expose the value added services offered by MEC, including real time access to network and context information, as well as location awareness. The design principles for developing the APIs have also been specified in ETSI GS MEC 009, along with http methods, templates, conventions and patterns. The MEC service APIs are available in YAML and JSON format at https://forge.etsi.org, presented via OpenAPI compliant descriptions.
MEC Sandbox provides the user with a choice of scenarios combining different network technologies (4G, 5G, Wi-Fi) and terminal types. Combining these assets in a geolocated environment, a user can gain hands-on experience on the behavior and capabilities of the Location (MEC013), Radio Network Information (MEC012) and WLAN Information (MEC028) service APIs. Such contextual information can offer significant differential performance for edge based MEC applications.
Web UI
MEC Sandbox Portal is a single page web application that provides an interactive interface; once signed in, it allows a user to experiment with an individual sandbox.
More details about the MEC Sandbox UI are provided in the platform usage section of this wiki.
Terminology
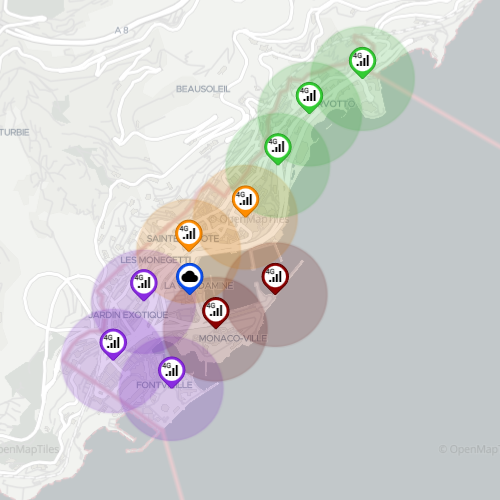
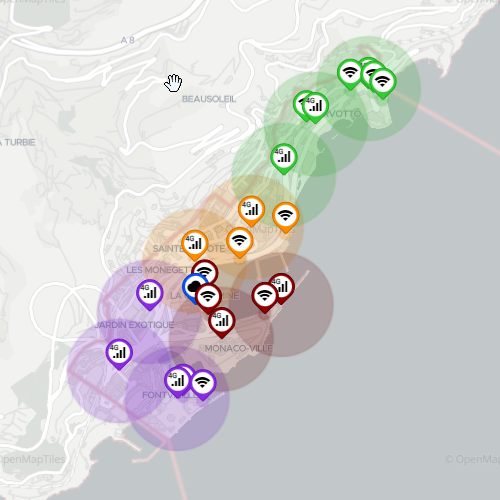
Point of Access (POA)
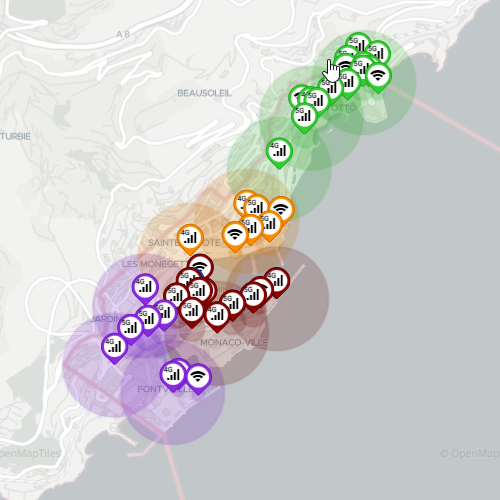
A point of attachment to access a network; MEC Sandbox networks supports 4G, 5G and WiFi POAs.
- Each POA has coverage range within which a terminal may attach to the network.
- The PoA range is represented by a circle and its the range varies depending on the network technology
- Both the PoAs and their associated range can be shown or hidden by selecting the appropriate layers on the map.
User Equipment (UE) / Terminal Device
A end user devices equipped with a wireless radio that allows to connect to a PoA.
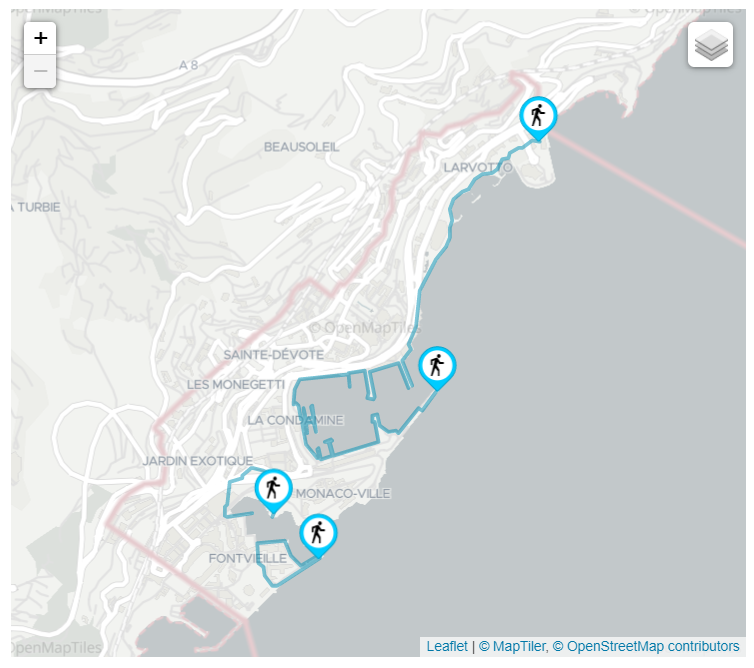
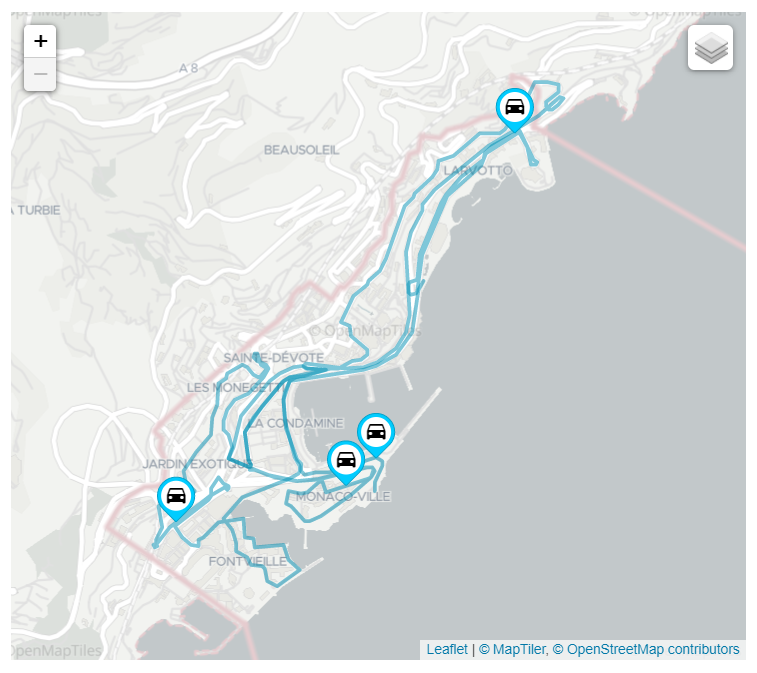
- MEC Sandbox supports three types of UEs; stationary, low-velocity and high-velocity
- UE types are described in more detail in this wiki section.
- Number of UEs present in a scenario can be configured
- Each UE has an associated velocity and path that defines how they move on the map; these are fixed in a scenario.
- UEs have their preferred access network types with their preferred order of connection
- Preferred connectivity order is (1) WiFi, (2) 5G and (3) 4G
- The default UE behavior is to remain connected to a POA as long as it is in range unless a higher priority network access becomes available.
Zone
A zone is a logical grouping of one or more PoAs, irrespective of their wireless technologies.
- On the map, zones are represented by using color coding.
- The definition of zones help structure the network.
- MEC Location Service (MEC013) can be used to discover zones or UEs present in a zone.
Network Scenario
A network of geo-located UEs and POAs that are grouped in Zones.
- One network scenario can be deployed at a time in a MEC Sandbox instance.
- At any time a user can terminate a scenario or select a new one without requiring to re-create a new sandbox.
- While a network scenario is deployed, requests can be sent to the MEC Service APIs which will return a response
- MEC Services may also generate notifications depending on the subscriptions created by the user
- Both responses and notifications reflect the state of the network at the moment they were generated
Network Scenarios
Networks
MEC Sandbox provides the following networks
UE Types
UEs are divided into the following categories:
The number of UEs in a network scenario is dynamically configurable, however the positions and paths are the same for all scenarios.
MEC Services
MEC012 - Radio Network Information Service (RNIS)
MEC Sandbox supports version v02.01.01 of the MEC012 specification, available on ETSI website
RNIS provides cellular radio network information to edge applications, such as:
- Radio network conditions
- Measurements related to user plane
- Information about UEs connected to the radio network (context, Radio Access Bearers (RAB))
- Notification events such as cell change, RAB establishment and RAB release
MEC Sandbox supports a subset of RNI API endpoints and subscription types; for more details on the supported endpoints access the SwaggerUI client in a MEC Sandbox.
MEC013 - Location Service
MEC Sandbox supports version v02.01.01 of the MEC013 specification, available on ETSI website
Location Service provides geospatial and network location information to edge applications, such as:
- Location information related to user and zones
- Notification events such as user tracking, zonal status or traffic
MEC Sandbox supports a subset of the Location API endpoints and subscription types; for more details on the supported endpoints access the SwaggerUI client in a MEC Sandbox.
MEC028 - WLAN Access Information Service (WAIS)
MEC Sandbox supports version v02.01.01 of the MEC028 specifications, available on ETSI website
WAIS provides WLAN radio network information to edge applications, such as:
- Access point conditions
- Information about terminals connected to the network
- Notification events such as terminal connectivity
MEC Sandbox supports a subset of the WAI API endpoints and subscription types. for more details on the supported endpoints access the SwaggerUI client in a MEC Sandbox.
Usage
The following section provides MEC Sandbox usage guidelines.
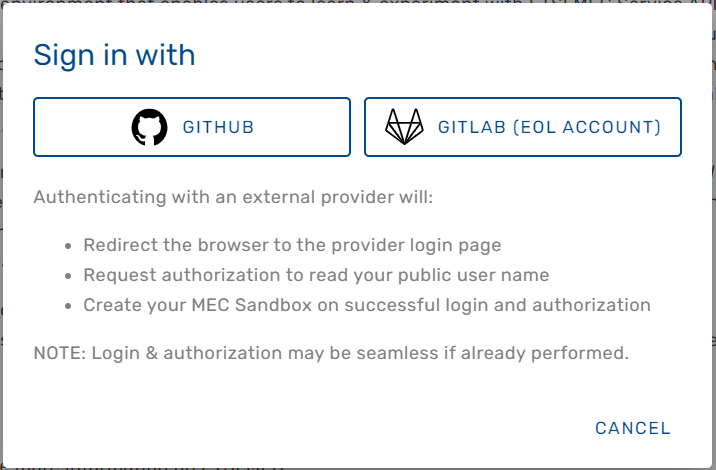
Sign In
The MEC Sandbox home page provides a Sign In button to initiate a user session. When clicked, the user is prompted to authenticate with one of the following external OAuth 2.0 providers:
To successfully sign in to the MEC Sandbox, the user must have a valid account with one of the above providers, must successfully sign in, and must accept an authorization request for access to public profile information. Once signed in and after successful backend resource allocation, the user is redirected to the MEC Sandbox dashboard. NOTE: External OAuth provider login and authorization may be seamless if they have already been performed |
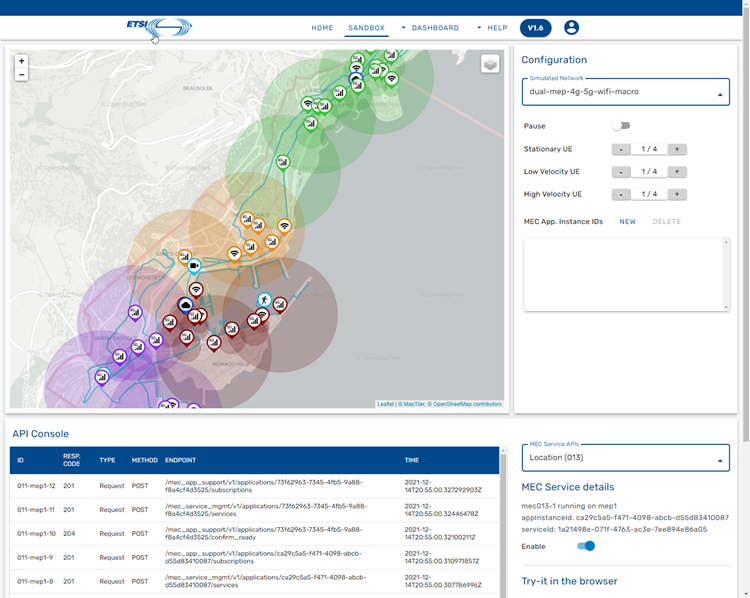
MEC Sandbox Dashboard
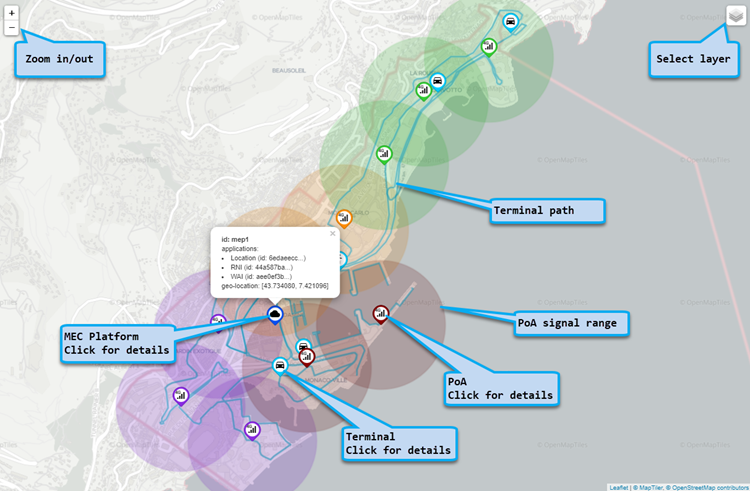
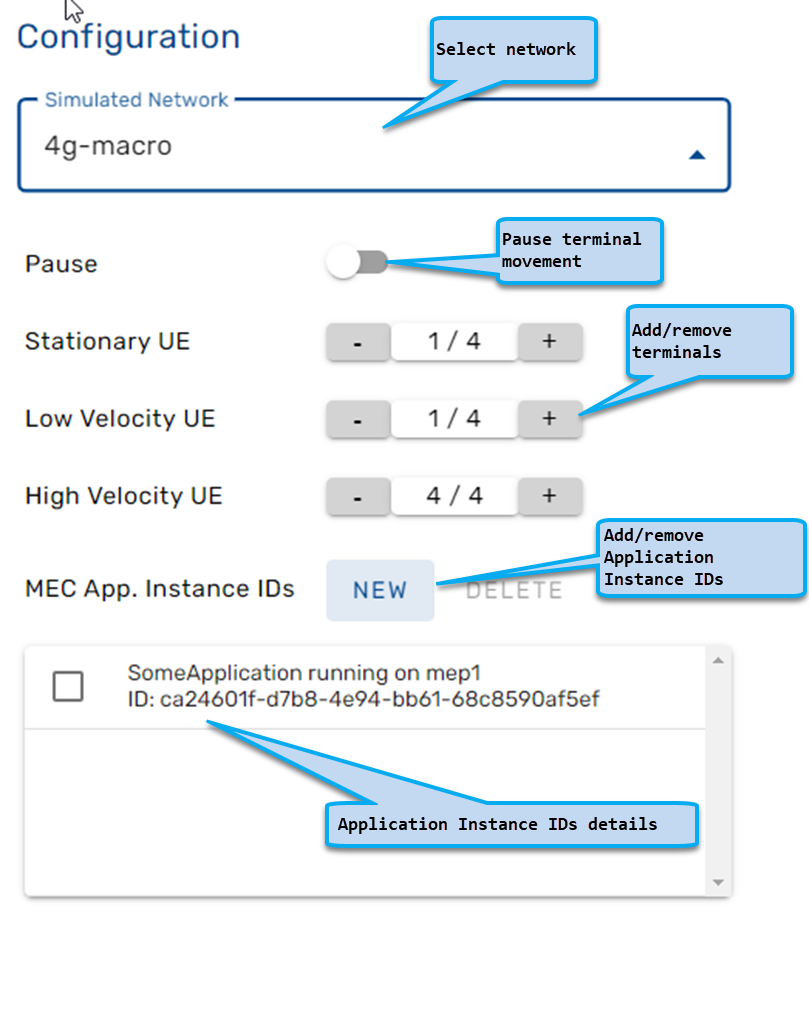
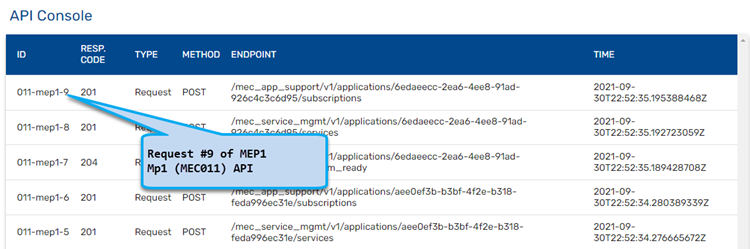
The dashboard is the main screen of the MEC Sandbox; it is divided in 4 main areas that are explained below:
- Map area: Observe physical assets on the map
- Configuration area: Select networks and UEs
- API Console: Investigate MEC API communication
- Try-it area: Details about accessing MEC Service APIs
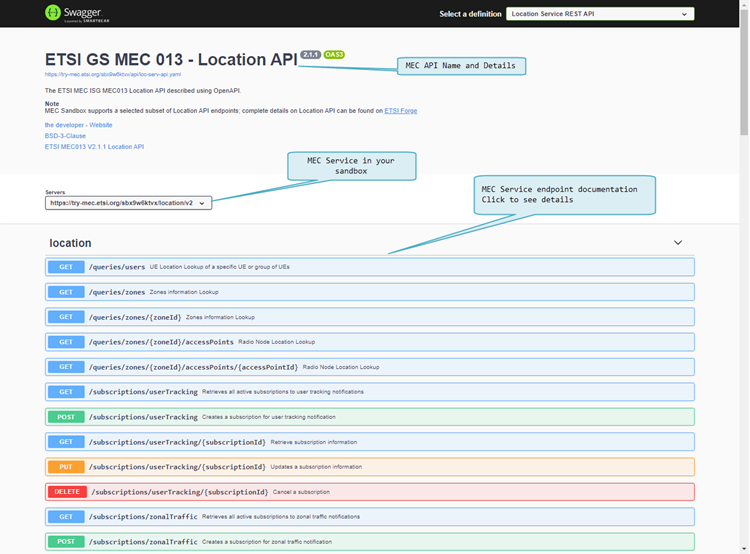
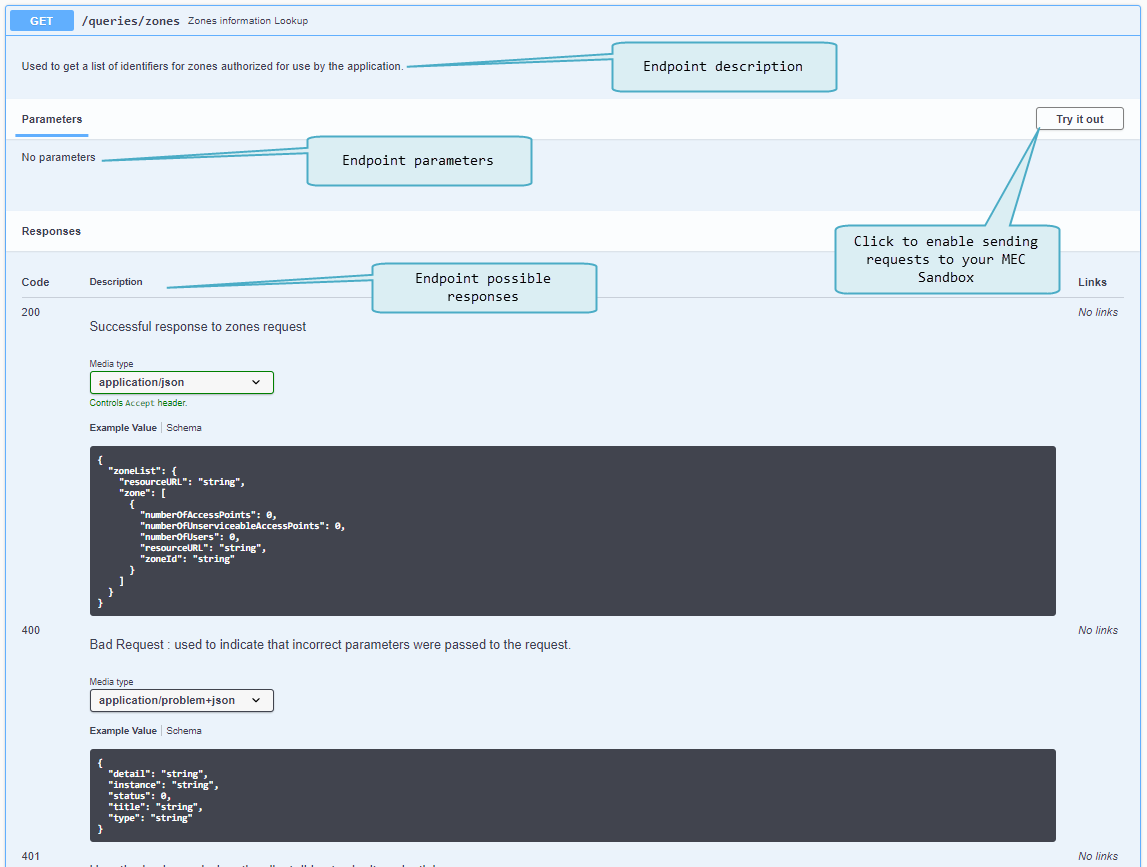
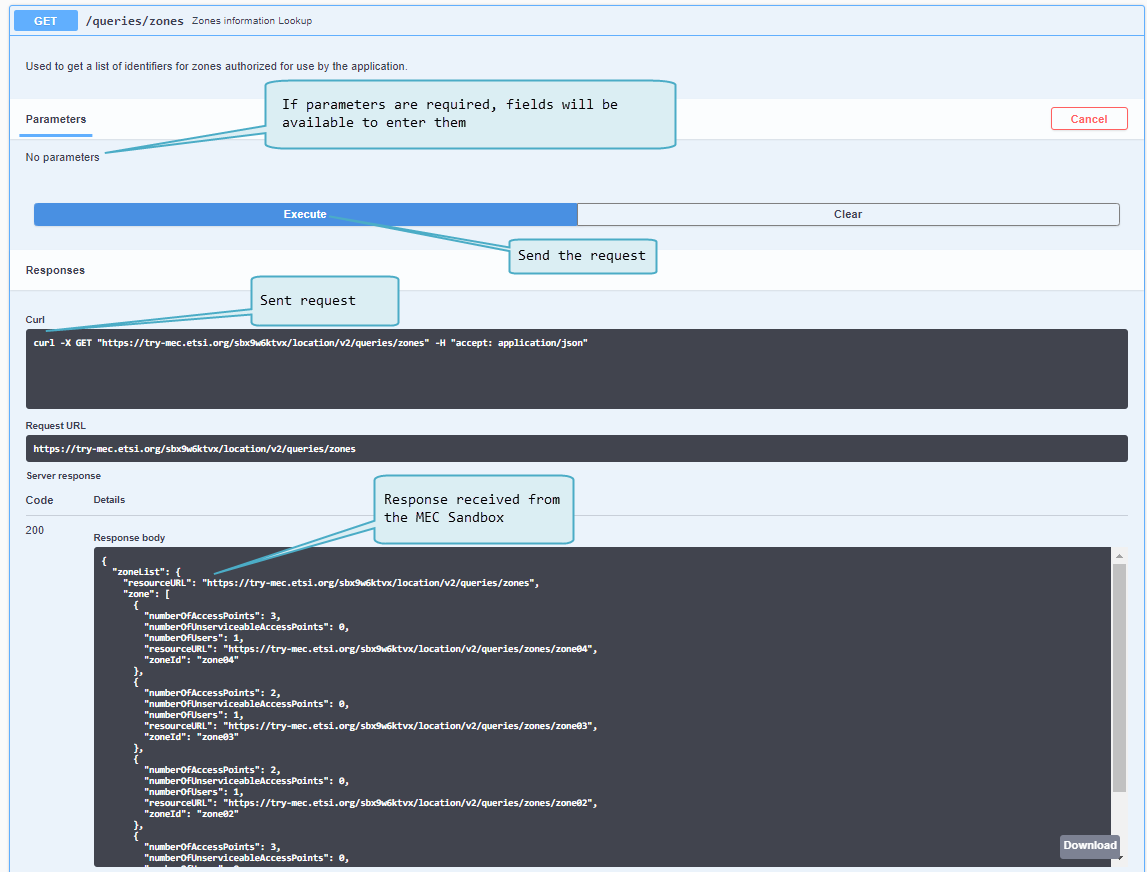
Swagger UI
The Swagger UI client is a powerful tool to learn about MEC APIs as it provides curated & browsable information about the API endpoints - but it also serves as an API client allowing to send requests and observe responses.
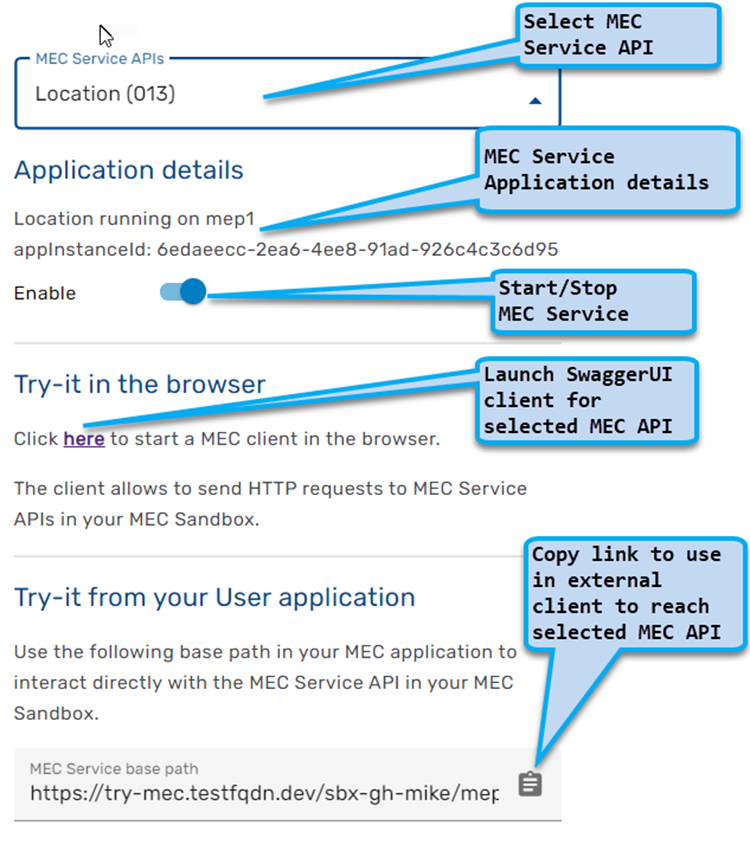
MEC Application
MEC Application developers can access MEC Services running in the MEC Sandbox using the base path URL provided in the Try-it area of the Sandbox dashboard. This link routes requests for the selected MEC API to a specific user sandbox.
NOTE: Any external application or process with HTTP client capabilities and access to the MEC Sandbox can be used to send requests to the MEC Services
MEC applications must use the provided link as a base path for API requests and must append the desired endpoint path. MEC applications must also provide path, query and body parameters when necessary. For more details on the supported endpoint paths and parameters, access the Swagger UI client in a MEC Sandbox.
For notification subscriptions, MEC applications must provide notification URLs where MEC Service notifications should be sent. If a notification URL points to a publicly accessible endpoint, the API Console will show the request and response data and codes; otherwise, the request will fail and the API console will display a 500 Internal error.
Examples
Work in Progress